How to Validate Email Addresses A B2B Guide to Perfect Deliverability

Validating your email list is single-handedly the most effective way to protect your sender reputation and make sure your campaigns actually hit the inbox. It’s a series of checks, from simple syntax corrections to more advanced server verifications, that confirm an email address is real, active, and safe to send to. For any B2B marketing strategy, this isn't just good practice—it's fundamental.
To give you a clearer picture of what's involved, here’s a quick rundown of the core checks that a proper validation process runs through. We'll dive much deeper into each of these throughout this guide.
Core Components of Email Validation at a Glance
These checks work together to give you a complete picture of your list's health, moving far beyond just basic bounce detection.
The Hidden Costs of an Unverified Email List
Ever wonder why a brilliant campaign just… flops? More often than not, the silent saboteur is a dirty email list. The damage from unverified emails goes way beyond a few bounced messages. It creates a ripple effect that can stall your entire growth engine.
Picture this: your team launches a meticulously crafted B2B newsletter, designed to nurture high-value leads. But you soon discover that 14% of your hard-earned subscribers are invalid. This isn't just a number. It represents wasted resources, skewed analytics, and a direct hit to your sender reputation—the very score internet service providers (ISPs) use to decide if you’re trustworthy or just another spammer.
Beyond Bounces: The Real Damage
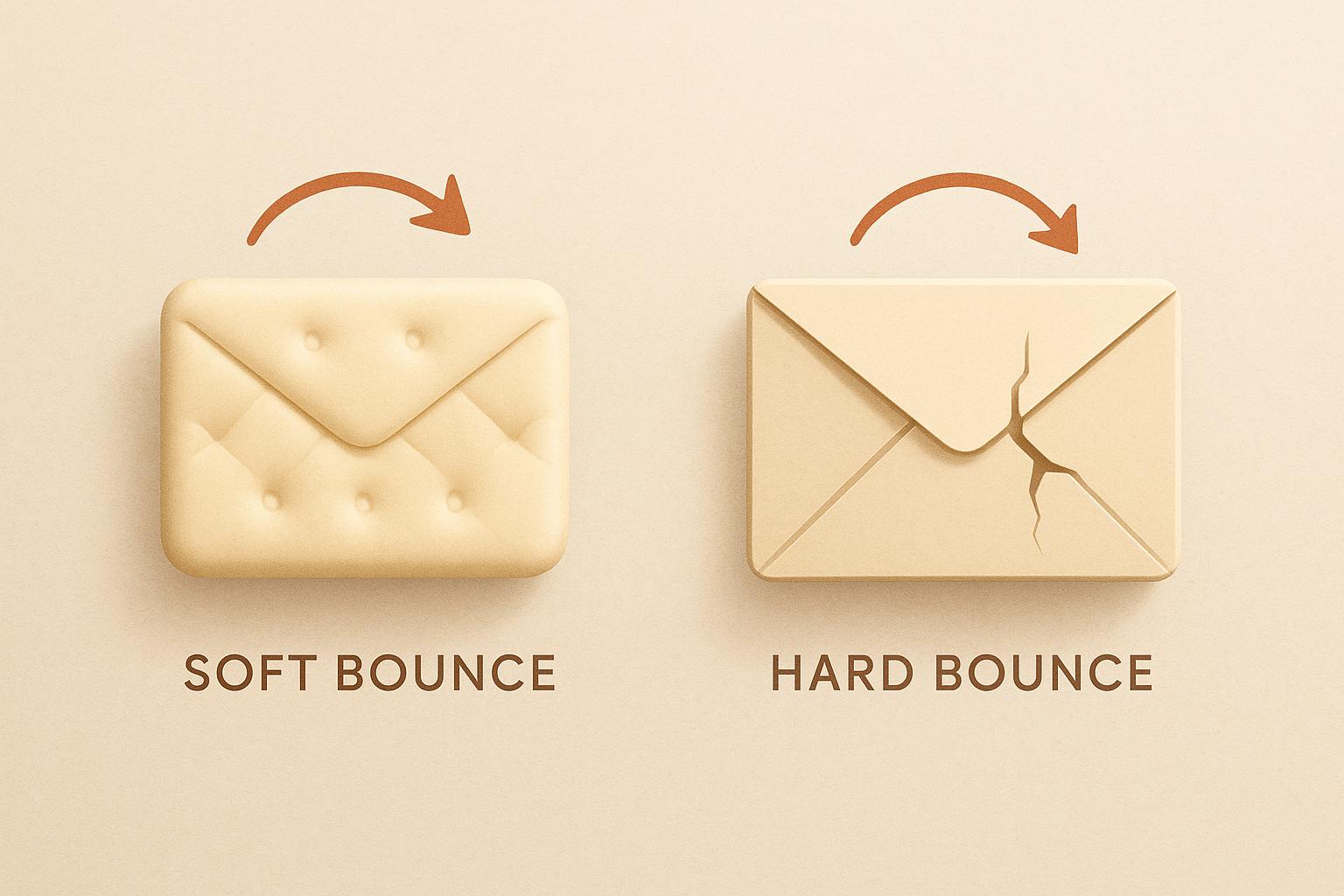
An unverified email address isn't just a dead end; it's an active threat to your marketing operations. Every single hard bounce sends a negative signal to ISPs like Gmail and Outlook, slowly chipping away at your sender score.
Once your reputation is damaged, even your valid emails are more likely to land in the spam folder, making them invisible to your most engaged prospects. It kicks off a costly chain reaction for your entire business that’s incredibly hard to reverse.
For B2B marketers, email validation is non-negotiable. It's not some technical chore you hand off to IT—it’s a strategic imperative for protecting your sender score and ensuring your most critical communications actually connect with your ideal customer profile (ICP).
This problem has a real financial weight. With global email volume constantly on the rise, businesses are facing staggering losses from undelivered messages. In the US alone, this adds up to over $59.5 billion annually, which breaks down to about $164 million every single day. For B2B marketers targeting specific accounts, the stakes are even higher, since each failed delivery is a missed opportunity with a high-value lead.
The Foundation of Successful Email Marketing
Ultimately, mastering email validation is the bedrock of any successful email strategy. It ensures your messages get delivered, your sender reputation stays intact, and your campaign ROI is based on clean, accurate data.
Without it, you're essentially marketing in the dark, just hoping your efforts find their way to the right people. If deliverability is already a struggle, our guide on how to reduce email bounce rates in B2B marketing can help, but remember: clean data is always the first and most important step.
Understanding the Layers of Email Verification
Effective email validation isn’t a single click. It's a sophisticated, multi-layered process, kind of like a security checkpoint at an airport. Each station checks for something different, and an email address has to pass through all of them to be considered truly valid and safe for your list. Knowing how to validate email addresses means understanding what's happening at each of these crucial stages.
This structured approach goes way beyond just checking for an "@" symbol. It systematically filters out typos, confirms the destination server actually exists, verifies the specific mailbox is active, and even flags potentially harmful or low-value contacts before they can tank your sender reputation.
The First Filter: Syntax and Format Checks
The most basic layer of validation is the syntax check. This is an automated review of the email's structure to make sure it follows standard formatting rules. Think of it as the first line of defense against obvious typos and incorrectly entered data.
An email address like john.doe@gmailcom (missing the dot) or jane.doe@.com (invalid domain format) gets flagged immediately. While it sounds simple, this step is absolutely essential for catching human error at the point of capture, like on a signup form or during a manual data entry task. This initial scrub prevents the most basic invalid addresses from ever getting into your system.
The Second Filter: Domain and MX Record Verification
Once an email passes the syntax check, the next step is to verify its domain. This involves two key actions that confirm the destination server is real and set up to receive mail.
- Domain Name System (DNS) Check: The validation service checks if the domain (the part after the "@" symbol, like
gmail.com) is a registered and active domain. If the domain doesn't exist, the email address is immediately marked as invalid. - Mail Exchanger (MX) Record Check: This is a more specific check. The service looks for MX records tied to that domain. An MX record tells the internet where to send emails for that domain. If a domain exists but has no MX records, it means it’s not set up to receive email, making the address undeliverable.
A valid domain with proper MX records confirms that a legitimate mail server is waiting to receive your message. It doesn't yet confirm the specific user exists, but it verifies the "address" of the building is correct.
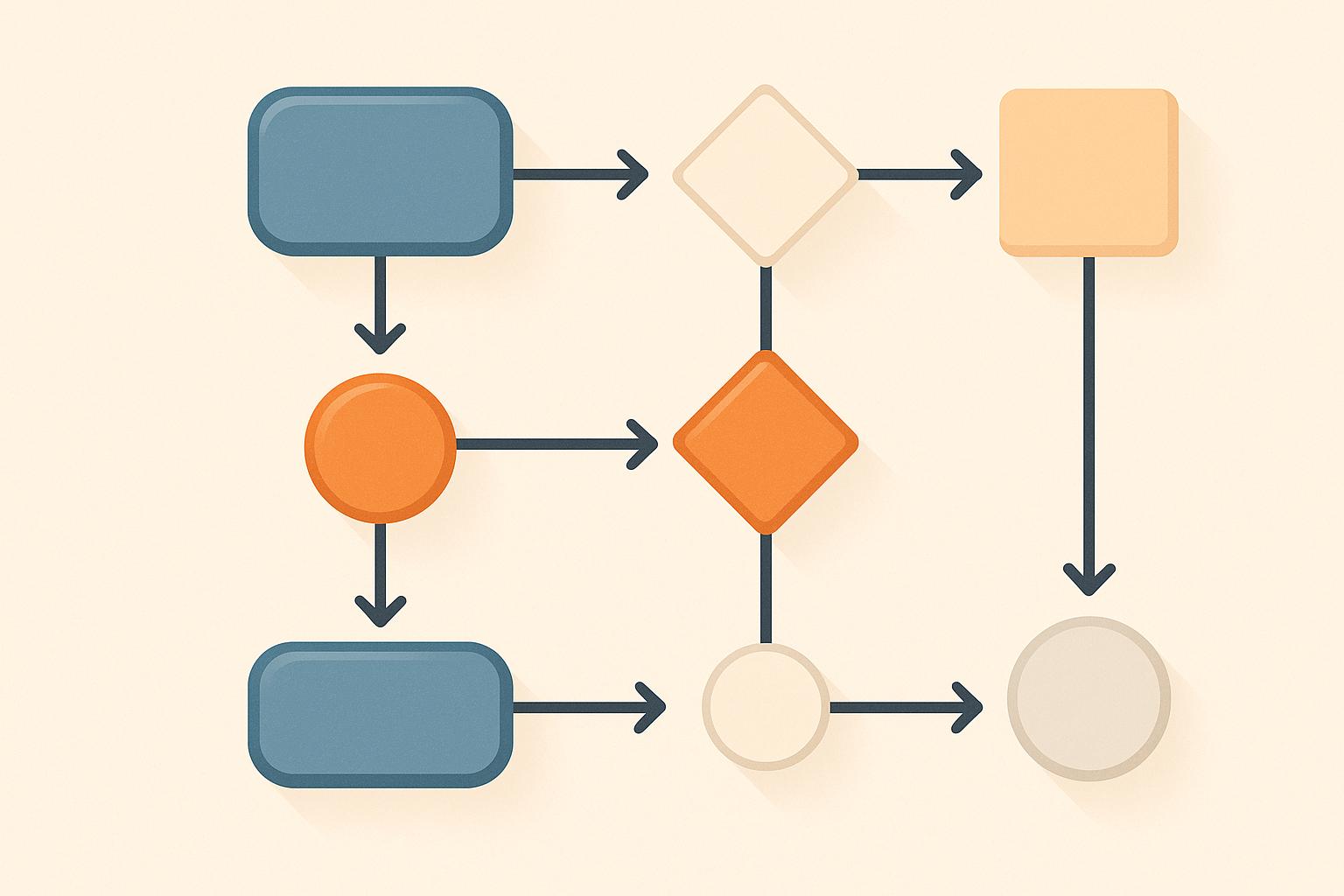
The process of weeding out these bad emails is critical. As you can see below, a bad list directly leads to reputation damage and, ultimately, lost ROI.

This flowchart illustrates the direct financial consequences of poor list hygiene, where each invalid address contributes to a negative cascade that hurts your bottom line.
The Third Filter: SMTP Verification
This is where the magic really happens. SMTP verification, often called a "ping," is the process of communicating directly with the recipient's mail server to ask if a specific mailbox exists. It’s like calling the front desk of an office building to ask if a particular employee works there.
The validation service initiates a handshake with the mail server without actually sending an email. It just simulates the first few steps of an email delivery and waits for the server's response. The server will reply with a code indicating whether the mailbox (john.doe) is valid, invalid, or unknown. This is by far the most accurate way to confirm an inbox is real and active.
Key Takeaway: An SMTP check is the only method that can definitively confirm if a specific user's mailbox exists on a server. This step is what separates basic validation from a truly comprehensive verification process that significantly reduces hard bounces.
The Fourth Filter: Advanced Detection
The final layer goes beyond simple validity to assess the quality and risk associated with an email address. A technically deliverable address isn't always a good address for a B2B marketer. This stage flags several types of problematic emails.
Commonly Flagged Email Types:
- Disposable Emails: These are temporary addresses from services like Mailinator that self-destruct after a short time. They are often used to access gated content without providing a real contact, resulting in zero long-term value.
- Role-Based Emails: Addresses like
info@company.com,support@, orsales@are valid but aren't tied to a specific person. Sending to these often leads to low engagement and can sometimes trigger spam complaints if multiple team members manage the inbox. - Catch-All Servers: Some domains are configured to accept email for any address, making it impossible for an SMTP check to confirm if a specific user exists. While deliverable, these are risky because they might be routing to an unmonitored inbox, and a high percentage can still bounce later.
- Spam Traps: These are email addresses used by ISPs and blacklist operators to identify spammers. Sending to one can get your domain or IP address blacklisted almost instantly, causing severe deliverability issues.
By identifying these addresses, you can segment them out or remove them entirely, ensuring your list is not just deliverable but also filled with high-quality, high-engagement contacts. This final, sophisticated check is what truly protects your sender reputation and maximizes campaign effectiveness.
Choosing Your Validation Workflow: Batch vs. Real-Time
Knowing the different layers of verification is one thing; putting them into practice is another. The next crucial step is deciding when and how to validate your emails. Your choice really comes down to two primary workflows: batch validation and real-time validation.
Each serves a distinct strategic purpose. One is perfect for cleaning up historical data you've had sitting in your CRM for years, while the other acts as a gatekeeper, protecting your list from bad data right at the source.

When to Use Batch Validation
Think of batch validation as a deep clean for your entire email list. You upload a file (usually a CSV) to a validation service, and it crunches the numbers, returning a detailed report on the status of every single address. It’s your go-to for periodic list hygiene and large-scale data cleanup.
You aren't going to do this every day, but it’s absolutely essential for maintaining the health of your existing contacts.
Here are a few classic scenarios for batch validation:
- Before a Major Campaign Launch: You’re about to launch a new product or drop a big announcement. Running your entire list through a batch validator beforehand ensures you get maximum deliverability and protects your sender score from a sudden spike in bounces.
- After Acquiring a New List: Just merged with another company or—let's be honest—bought a contact list? Before you even think about importing those thousands of new emails into your system, a batch clean is completely non-negotiable.
- Quarterly or Bi-Annual List Cleaning: Email addresses decay over time. People change jobs, abandon old inboxes, or make typos. A regularly scheduled batch validation keeps your master list fresh and accurate.
Batch processing is all about proactive maintenance. It tackles the natural degradation of data and gets your existing assets ready for high-stakes campaigns, making sure you’re always working with the cleanest possible list.
When to Use Real-Time Validation
Real-time validation, on the other hand, is all about prevention. Typically handled via an API, it checks an email address the very instant it's submitted, stopping bad data from ever entering your ecosystem in the first place.
This is your front-line defense. It integrates directly into your lead capture forms—think webinar sign-ups, demo requests, or newsletter subscriptions—providing immediate feedback.
Say a user enters
john@gmil.com(a classic typo) into your form. A real-time API instantly flags the error and prompts them to fix it before the submission goes through. This simple interaction prevents a bad lead from ever polluting your CRM and skewing your data.
This immediate feedback loop is critical. It improves the user experience by helping visitors correct honest mistakes and guarantees that every new lead you capture is valid and deliverable from day one.
The rise of real-time validation coincided with the explosion of the email marketing software market. Industries that adopted it quickly, like sporting goods, saw workflow click rates as high as 6.22%, while those that lagged behind struggled. This historical shift underscores just how important modern data hygiene is for maintaining a strong sender reputation. You can explore more about the email industry's evolution and its impact on marketing strategies.
A Direct Comparison
Choosing between batch and real-time isn't an either-or decision; most effective strategies use both. Here’s a quick look at how they stack up.
Comparison of Batch vs. Real-Time Validation Workflows
Ultimately, any strong B2B growth team needs a dual approach. Use batch validation to regularly maintain the integrity of your existing database, and implement real-time validation on all your lead capture points to ensure a constant stream of high-quality, verified contacts.
How to Weave Validation into Your Growth Stack
Theory is great, but putting it into practice is what actually drives growth. So, now that we've covered the different validation workflows, let's talk about getting this stuff working inside your existing marketing tools. The real goal isn't just to clean a list once; it's to build automated, ‘set-it-and-forget-it’ systems that keep your data pristine without you having to think about it.
When you seamlessly connect validation services with your core platforms—your CRM, newsletter software, and lead capture forms—you graduate from occasional cleanups to a state of continuous data integrity. This is how you build a growth engine that scales.
Connecting to Your CRM
Your CRM is the heart of all your customer data. Plugging an email validation service in here ensures the information your sales and marketing teams depend on is always accurate. Most modern validation platforms offer direct integrations or use connector tools like Zapier to link up with CRMs like HubSpot and Salesforce.
A typical setup involves a workflow that kicks off a validation check whenever a new contact is added or an old one gets updated.
For example, a common HubSpot workflow looks like this:
- Trigger: A new contact is created from any source (like a form submission or a manual import).
- Action: The contact's email address is automatically pinged to your validation service's API.
- Update: The result—like "Valid," "Invalid," or "Risky"—is written back to a custom property field on that contact’s record.
With this simple automation, you can start building active lists based on validation status. You could, for instance, create a segment of all "Invalid" contacts to be scrubbed from your marketing campaigns, which directly protects your sender reputation. To really get into the weeds on making these connections work, check out this ultimate guide to CRM and email integration.
Automating Validation in Newsletter Platforms
For platforms like Breaker or Substack, where your newsletter is the product, list hygiene is everything. Integrating validation directly into these tools stops bad emails from ever polluting your audience in the first place.
Many services have native integrations that sync with your lists and run automated cleaning on a schedule you set. You could, for example, tell the integration to run a full validation on your entire subscriber list every 30 days. This process can automatically tag or unsubscribe contacts flagged as invalid, disposable, or spam traps, keeping your deliverability sky-high for every send.
By automating this process, you shift from reactive list cleaning to a proactive hygiene strategy. Your list stays clean in the background, freeing you up to focus on creating great content instead of worrying about bounce rates.
Fortifying Your Lead Capture Forms
Honestly, the most effective way to keep a clean list is to stop bad data at the door. Integrating a real-time validation API with your lead capture forms is the single best thing you can do.
This applies to every single form you use:
- Webinar registration pages
- Demo request forms
- Gated content and lead magnet sign-ups
- "Contact Us" pages
Here’s how it works: a user types in their email and hits "submit." In that split second, the API checks its validity. If they made a typo like contact@gamil.com, the form can fire back a friendly message like, "Did you mean gmail.com?" This simple interaction not only improves the user experience but guarantees only clean, verified data enters your system.
This preventative step is far more efficient than cleaning up a messy database later. It ensures every new lead is deliverable from the moment they sign up, maximizing the impact of all your inbound marketing efforts. When you bake validation into your entire growth stack, it stops being a chore and becomes a continuous, automated asset for your business.
Navigating the Trickier Side of Validation
Email validation gets a lot more interesting once you move past the simple syntax and domain checks. This is where you run into the real-world complexities—mail servers that are actively designed to push back against the very verification attempts you’re trying to make.
Getting a handle on these advanced challenges is what separates a decent validation process from a great one. Two of the biggest hurdles you'll face are rate limiting and greylisting. These are clever defense mechanisms that mail servers use to fend off spam and prevent overload. While they’re great for server admins, they can easily fool basic validation tools, causing them to flag perfectly good emails as "unknown" or "invalid."
Dealing with Rate Limiting
Rate limiting is exactly what it sounds like. A mail server will only accept a certain number of connection requests from one source in a given timeframe. Think of it like a bouncer at a popular club who only lets in a few people every minute to keep the place from getting swamped. Servers do the same thing to stop a single sender from hammering them with connections.
If your validation service tries to check thousands of emails on the same domain all at once, the server will slam the door. It will start temporarily rejecting connections, making it impossible to perform the SMTP handshake needed to verify the address.
A smart validation service knows how to work around this. They typically do two things:
- Use a Distributed Network: Instead of firing off all requests from one IP address, they use a global network of servers. This spreads the validation attempts across many different sources, making them look like unrelated traffic and flying right under the server's rate-limiting radar.
- Implement Intelligent Throttling: The best platforms can actually detect when a server is starting to push back. They’ll automatically slow down, wait, and retry at a pace the server is comfortable with. It’s a patient approach that ensures they get an accurate result without getting blocked.
Understanding Greylisting
Greylisting is another anti-spam tactic, but it's a bit more crafty. The first time an unknown server tries to connect, the receiving server will temporarily reject it with a "try again later" message. The logic is that legitimate, properly configured mail servers will do just that—they'll wait a bit and try again. Most spam bots, on the other hand, won't bother.
You can probably see the problem this creates for simple validation tools. They make one attempt, get the temporary rejection, and immediately mark the email as "invalid." It's a false negative.
A robust validation provider is built for this. Its systems are designed to recognize a temporary greylisting rejection, wait the appropriate amount of time, and then reconnect to finish the job. That patience is absolutely critical for getting accurate results from servers using this defense.
The Importance of Privacy and Compliance
Beyond the technical hurdles, you have to navigate the legal landscape. When you upload a list of contacts to a third-party service for validation, you're sharing personally identifiable information (PII). That single action puts both you and your provider under the microscope of data privacy laws like GDPR in Europe and CCPA in California.
Choosing a non-compliant provider isn't just a minor oversight; it's a massive legal and financial risk. Your process for validating email addresses has to be just as compliant as it is effective.
When you’re vetting a validation service, you absolutely have to dig into their commitment to privacy. Look for crystal-clear policies on how they handle, retain, and secure your data.
Key Compliance Questions to Ask a Provider:
- Are you GDPR and CCPA compliant? They should be able to provide clear documentation, not just a simple "yes."
- How do you secure my data? Ask for specifics on encryption, both for data in transit (as you upload it) and at rest (while it's on their servers).
- What is your data retention policy? Reputable services will permanently delete your lists from their systems shortly after processing is complete. Your data shouldn't live on their servers indefinitely.
- Do you ever share or sell customer data? The answer to this must be an unequivocal "no."
Picking a provider that can prove its compliance is foundational. It ensures your efforts to clean up your data don’t accidentally create a much bigger, more expensive problem down the road. It’s all part of building a responsible and trustworthy email program.
Measuring the ROI of Your Validation Efforts
So, how do you prove that all this validation work is actually worth the time and money? This is the final, crucial step: connecting your efforts to tangible business results. It’s how you get buy-in from stakeholders and elevate list hygiene from a simple technical task to a core driver of business growth.
The key is to look beyond the obvious metrics. Sure, a lower bounce rate is a great start, but the real value is in the downstream effects. You need to show how a clean list directly fuels better campaign performance and, ultimately, revenue.
Key Performance Indicators to Track
To really demonstrate the impact, focus on a simple before-and-after analysis. Compare your campaign metrics from the period right before you implemented a solid validation strategy to the period just after.
Here are the core metrics you should be watching:
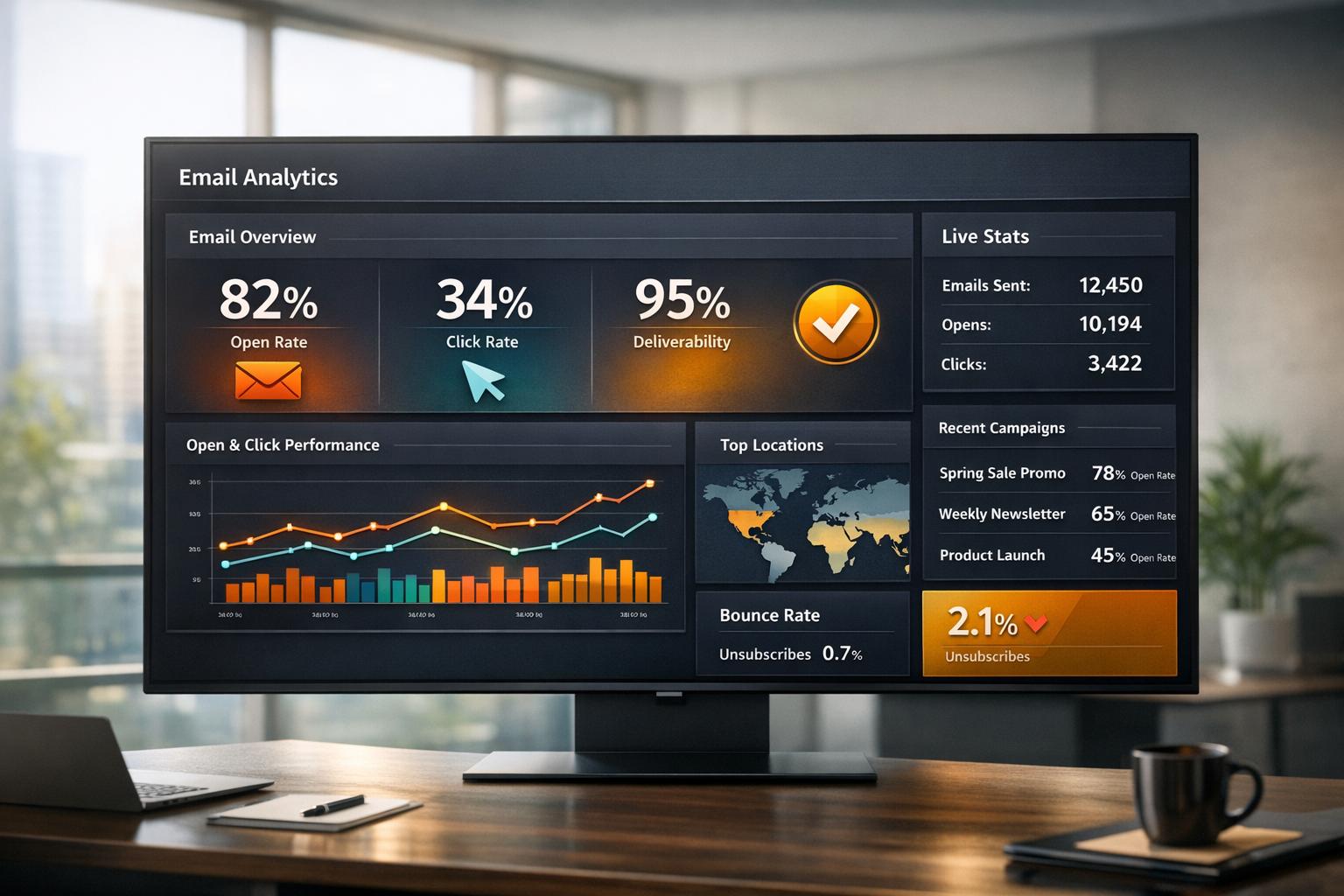
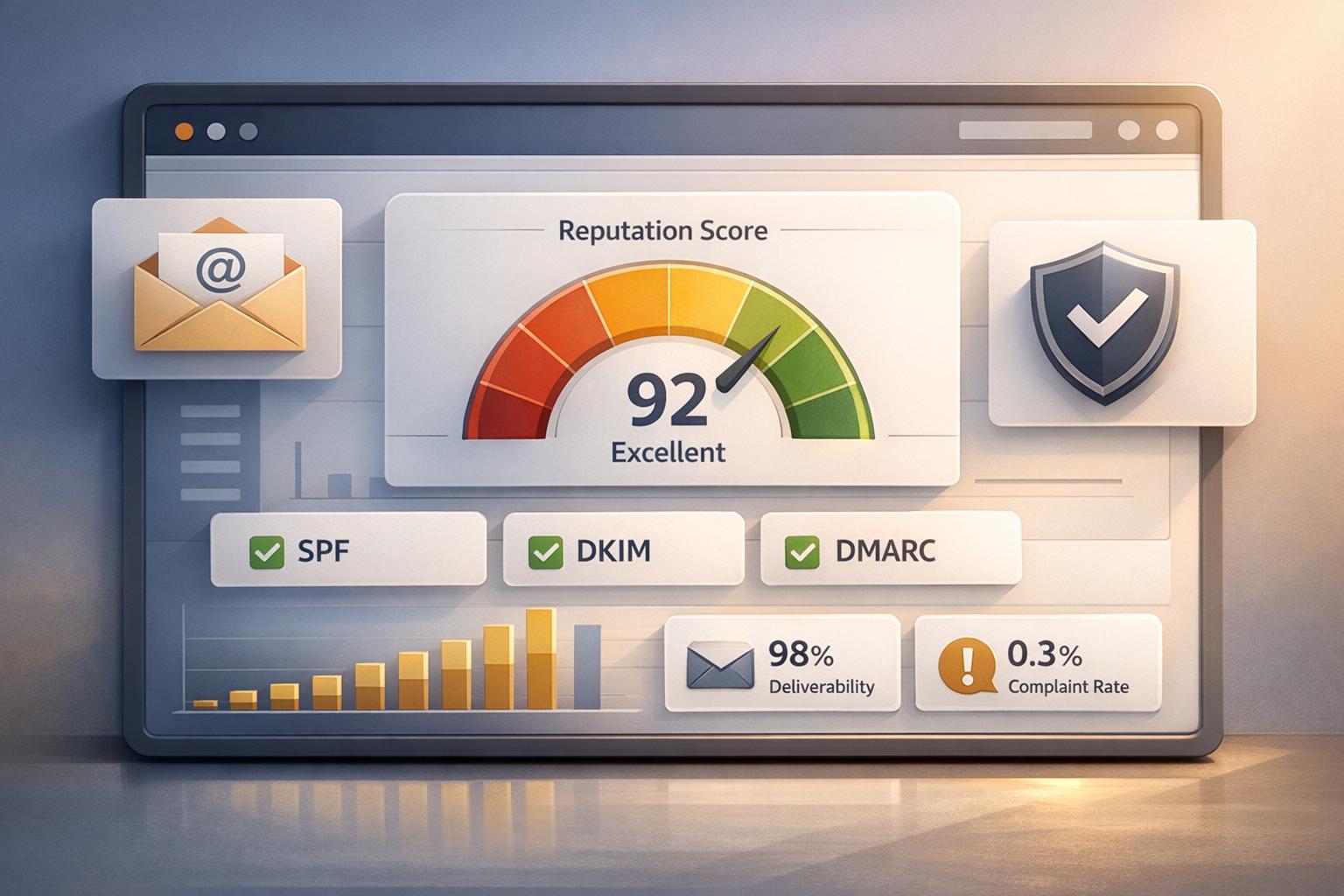
- Sender Reputation Score: Keep an eye on your score using tools like Sender Score from Validity. A rising score is direct proof that ISPs are taking you more seriously.
- Inbox Placement Rate: This is the big one—the percentage of your emails that actually land in the primary inbox instead of the spam folder. A higher rate means more prospects are actually seeing your message.
- Open and Click-Through Rates (CTR): When your emails consistently hit real, engaged inboxes, your open and CTR will naturally climb. This is a clear sign that your content is finally reaching a genuine audience.
- Conversion Rates: This is the ultimate metric. Track how many people are taking the action you want, whether that’s booking a demo, downloading a whitepaper, or making a purchase. An increase here shows that better deliverability leads directly to more business.
By framing the conversation around these impactful KPIs, you shift the focus from cost-saving (fewer bounces) to revenue generation (higher conversions). A clean list isn’t just about dodging problems; it’s about creating real opportunities for growth.
Building Your Business Case
With this data in hand, you can build a powerful story. For instance, you could present findings like this: "After implementing real-time validation, our inbox placement rate jumped by 15%. This led to a 10% lift in CTR and a 5% increase in demo requests from our newsletter campaigns."
That kind of specific, data-backed analysis makes the value impossible to ignore. If you want to dive deeper into the financial side of things, our article on how to calculate email campaign ROI gives you a framework for tying these metrics directly to dollars and cents.
Proving the ROI of knowing how to validate email addresses effectively ensures it stays a top priority in your marketing strategy.
Got Questions About Email Validation? We've Got Answers
When teams start digging into email hygiene, a few common questions always seem to surface. Let's tackle them head-on with some practical advice.
How Often Should I Validate My Email List?
This really comes down to how you're getting your leads. If you're working with a more or less static list, running a validation check once a quarter is a solid baseline to catch natural email decay. People change jobs, and addresses go stale. It happens.
But if you're in B2B and constantly pulling in new leads through demos, webinars, and content downloads, you can't afford to wait. You need continuous, real-time validation right at the point of capture. This is the only way to stop bad data from ever poisoning your CRM or marketing platform in the first place.
Can Email Validation Hurt My Sender Reputation?
Not if you're smart about it. Using a reputable, professional validation service is perfectly safe and won't ding your sender score. These platforms use secure, non-intrusive methods like server handshakes to check an address—they never actually send an email from your domain.
The danger comes from sketchy, low-quality services that might use risky practices. So, the takeaway is simple: stick with a trusted provider, and your reputation will be fine. In fact, it will improve because you'll be sending to a cleaner, more deliverable list.
What about "catch-all" servers?
You'll inevitably run into these. A catch-all server is set up to accept mail for any address at that domain, which makes it impossible to confirm if a specific inbox actually exists. While these emails are technically deliverable, they often have low engagement and can be a risk. It's usually best to segment them out or treat them with extra caution.